
23 Sep How Public WiFi Networks Puts Your Data At Risk
It is expected that the number of WiFi hotspots is to quadruple by 2015 giving users the ability to connect to approximately 5.8 million public hotspots worldwide says informa.
This means that in the very near future you can be connected no matter where you are: in parks, at popular tourist attractions or transport hubs. This is great for remaining productive, particularly for mobile workers.
However, with great connectivity comes great security risks.
Common Hacking Practices
Unfortunately, those using public hotspots have become a preferred target for hackers.
Due to their lack of security, public hotspots make it easy for even novice hackers to obtain sensitive personal or corporate data. How can they do this? We’ve outlined a few of their methods below.
Man in the Middle Attack (MITM)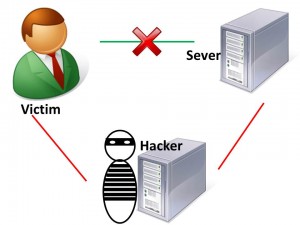
As the name suggests, a ‘Man in the Middle Attack’ involves a hacker intercepting or modifying information sent between two devices by impersonating both parties. This type of attack allows a hacker to intercept, send, and receive data meant for someone else, or not meant to be sent at all, without either outside party knowing until it is too late.
Example
You’re in a hotel lobby waiting to meet a client.
From your laptop, you log into the public WiFi network of the hotel so you can access some documents for your meeting. Among those documents is rather sensitive client information.
If a hacker decides to listen in on what your device is sending and receiving, he could easily intercept any sensitive data you are accessing. All without your knowledge.
Rogue WiFi Networks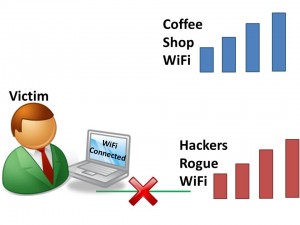
A Rogue WiFi Network, often called an ‘Evil Twin’, is a hotspot created by a hacker masquerading as a legitimate hotspot. If the user connects to the rogue WiFi network, the hacker can capture the user’s passwords, gather sensitive information and direct the user to malicious websites.
Example
You walk to a coffee shop you frequently visit, ready to get some work done. Using your tablet, you connect to what you think is the coffee shop’s public WiFi to access your work email.
This is something you’ve done on several occasions. Only this time, the WiFi network you have connected to does not belong to a coffee shop but is instead an ‘Evil Twin’. The hacker now has access to every single one of your work emails and any other corporate data on the tablet that is unencrypted.
Connect to WiFi Networks Automatically
To reduce cellular data usage, it’s common practice for users to keep their WiFi setting switched to ON, constantly searching for WiFi networks to connect to. This allows the device to automatically connect to a public WiFi network when one is found. However, by allowing your device to connect to open WiFi networks automatically, it increases your chances of connecting to a network created by a hacker.
Example
During you’re lunch break, you’re having lunch in a food-court and your default setting is to connect to public WiFi networks automatically. Your device has connected to a WiFi network created by a hacker. Without realising it, you’ve opened the door for the hacker to access unencrypted corporate data from your device.
Protecting Your Data
Don’t open or send any sensitive corporate information over public WiFi networks. Use your cellular data or wait until you are connected to a secure WiFi network.
Ensure the web address you are using begin with HTTPS instead of just HTTP. This indicates that the website is using encryption and information you exchange will be confidential.
Use comprehensive security software on your devices to increase your protection against malware.
Be wary of any request for personal information when you are not using cellar data or a trusted WiFi network.
Manage the WiFi settings on your device. Ensure your device does not automatically connect to open WiFi networks.
Education is key, so ensure you are aware of how your device can be compromised and take the necessary steps to protect your device and your data.
While there are many more ways your device can be compromised, by using the tips we’ve provided you can help protect your device and your data when connected to a public WiFi network. Always use caution when accessing sensitive data and where possible try to use your cellular data instead of public WiFi networks.
Do you have any other tips on protecting your data? Let us know in the comments below!

